IN 1508 – Cyber security considerations for autonomous and remotely controlled systems
- Information Note
- Published on 11 June 2020
- 6 minute read
Jump to:
1. A Brief history of security
Historically, security can be defined as:
- The state of being free from danger or threat.
- The safety of a state or organization against criminal activity such as terrorism, theft, or espionage.
- Procedures followed or measures taken to ensure the security of a state or organization.
The definitions still hold true today, but the methods used to ensure security are constantly changing. Traditionally, security of possessions has been implemented using physical barriers to protect possessions such as doors, padlocks, locked cabinets and supplemented by camera systems, access control, security guards, security dogs etc. Personal valuables may be held in bank safety deposit boxes which themselves are contained within locked vaults underground.
Documents, essentially items of data, were stored in secure filing cabinets to protect sensitive information being accessed by unauthorised parties.
With the advent of the digital age, almost all businesses underwent a digitisation process with documents being transferred onto digital media. With data now stored in digital formats, on computers and peripherals, access control became a less tangible process implemented through the use of passwords and cryptology, although an organisations computer storage facilities still maintained physical barriers, access controlled doors and areas, security cameras and guards. Access control advanced to include fingerprints, retinal scans, facial and voice recognition. Offices containing computers which hold sensitive data would also be protected with the more familiar security methods, locked doors, security patrols and cameras in addition to passwords.
With the creation of the internet and network computing, where remotely located computer systems could communicate and share data, a new threat appeared, Cybercrime.
2. Cybercrime in the UK
For the year ending March 2018, the UK Office for National statistics (ONS) released its Crime Survey for England and Wales (CSEW), showing that 4.5 million cybercrimes were committed; of these, 3.24 million were fraud related and 1.23 million computer misuse related (this includes hacking crimes). These crimes affected around 17 million UK citizens and resulted in the loss of £130 billion being stolen.
The London based Willis Towers Watson consultancy estimate that human errors led to 90% of cybersecurity claims it has assessed.
The most frequent types of cybercrime are:
- Phishing: where you receive an email that pretends to be from an authority (perhaps your bank, or maybe your boss) in which you’re asked to give out your passwords or personal information such as your address, telephone number, or other data.
- File Hijacking: where a hacker enters your computer and accesses your files, locking you out of them. The hacker then demands a ransom (usually money) before he will give you your files back.
- Webcam Managing: where hackers take over your webcam. This may be so that they can watch your keyboard and learn your passwords, or it may be to record video of you doing something personal that they can then blackmail you with, or perhaps just to learn personal information about you.
- Screenshot Managing: where hackers enter your computer and take screenshots of your display. This can help them get information about you, get passwords, or even blackmail you.
- Keylogging: where hackers can record your keystrokes on your computer, thus gaining your passwords or other personal info.
- Ad Clicking: where hackers encourage you to click on a link (perhaps by email, or on a webpage) which will then open malware or simply ask for your personal info.
Whilst many of the methods above are used on private individuals, they may also be used against businesses along with:
- Hacking: where hackers enter a business’s files or servers and gain information from them.
- Denial of Service (DOS) and distributed DOS (DDOS) attacks: where hackers enter a business’s files or servers and change them so that their services or web pages can’t be accessed.
If a business is subjected to an attack and its data is stolen many individuals may also be affected as harvesting personal data is often the reason for such an attack.
3. Cybercrime around the world
According to reports (Cybriant) as much as 0.8% of global GDP is lost to cybercrime. In 2017, cybercriminals extorted around $1.5 trillion globally, with $5 million attributed to ransomware. It is estimated that over the next 5 years, private companies could lose more than $5 trillion dollars to cybercrime. 53% of cyber-attacks result in average losses of over $500,000.
Large corporations and government departments are under constant threat from cyber attackers; many of these attacks are carried out by highly organised criminal outfits but others appear to have their sources within some foreign government departments.
4. Cybercrime and the potential threat to autonomous and remotely controlled systems
Note: there are several acronyms used for these vessels; Marine Autonomous Surface Systems (MASS), Unmanned Surface Vessels (USV). There are also ROV and AUV systems able to be operated from remote control centres (RCC), often referred to as unmanned underwater systems (UUV) and also unmanned aerial vehicles (UAV) usually known as drones. Cyber security is relevant to all such systems.
As Information Technology (IT) has advanced, the opportunity for cybercrime has also increased. Technological advances now make USV’s common place within a few years. Many such small craft (“Technologies, processes, and practices designed to prevent malware from doing damage or harm to networks, computers, programs, or data.”
But modern, distributed, interconnected remote systems demand a more comprehensive and robust OT based cyber security system which can be defined as:
“Technologies, processes, and practices designed to prevent the intended or unintended use of a cyber technology system to do damage to the cyber technology (networks, computers, programs, data), and vessel or harm to people, and environment.”
To achieve this level of protection we need to be able to verify the satisfactory performance of the OT cyber security system by:
- Ensuring correct, safe, efficient, and reliable operation through software quality engineering.
- Preventing malicious and non-malicious threats through the cybersecurity system.
Functional testing will help assess a system against ‘known’ errors or threats but makes no allowance for unknown events. Using a maturity model provides ongoing monitoring, assessment and improvement to a cyber security system and will help defend against these unknown events.
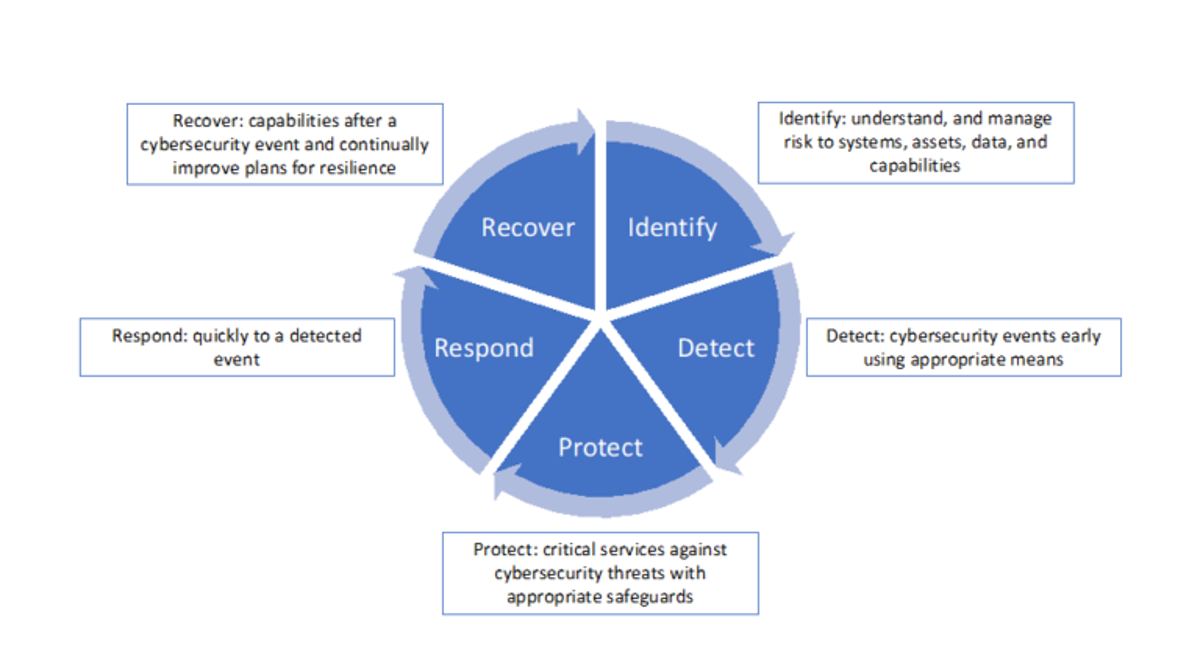
To be comprehensive, an evaluation of any system must include the processes used by the technology system owners, designers, users and suppliers, and should consist of active audit and testing of known threats, access points and protection from potential threats such as spoofing and phishing using penetration and scanning tests.
One final consideration is the stage, in the life cycle, where these security measures are applied. Ideally the security measures should be integrated as part of the initial designs. Robust security systems are much harder to ensure when viewed as an afterthought and their safety is harder, maybe impossible, to ensure. Each component of a system, where threat access could occur, should have adequate threat protection designed and built it by the equipment manufacturers.
Originally issued with the following reference(s): IMCA DIG 03/20.